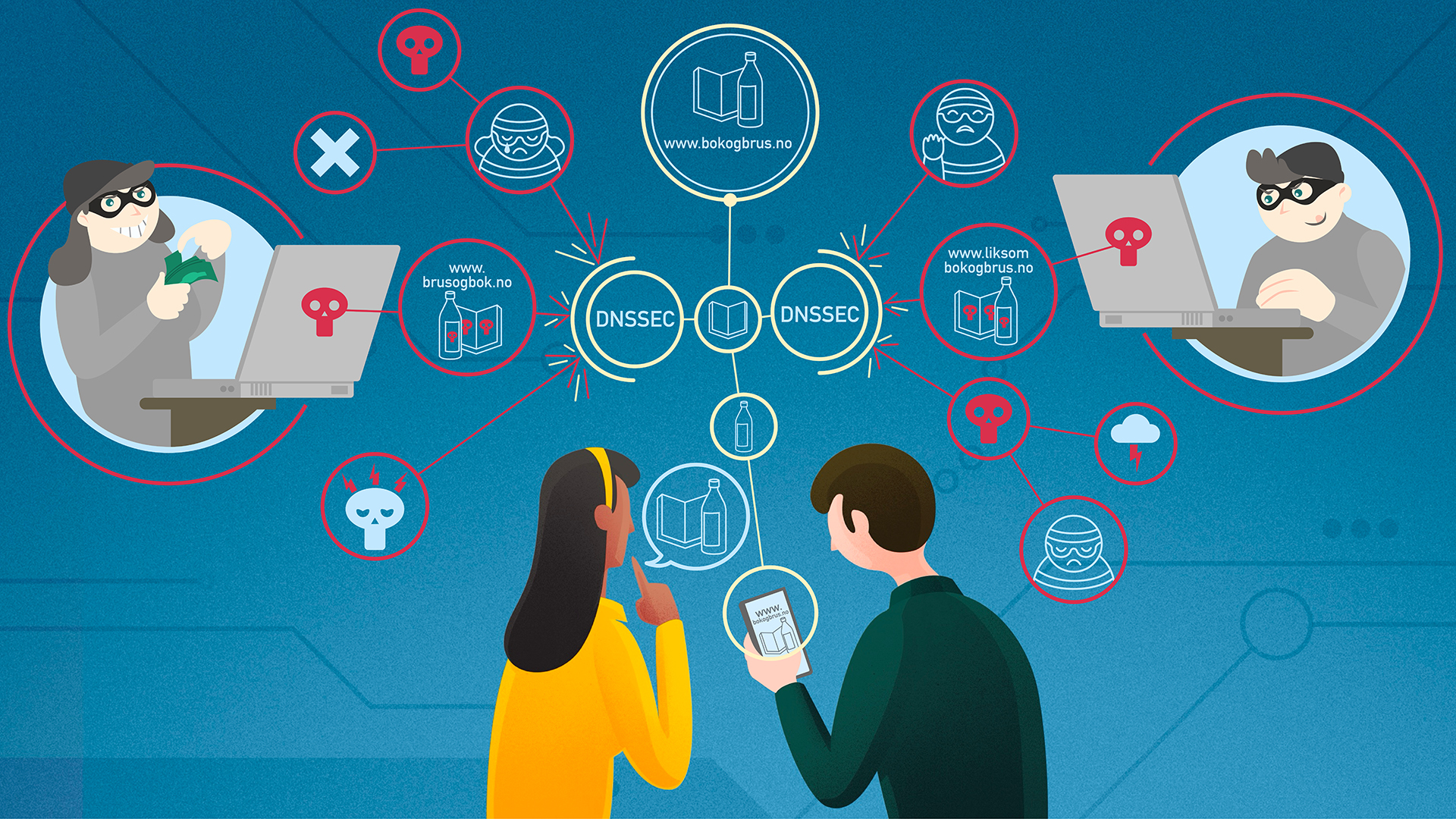
Why is DNSSEC important?
The Internet has become a key platform for value-creation in modern society. The Internet is also a primary channel of communication between public agencies and the nation’s inhabitants and businesses, e.g. in connection with tax returns, employer's contributions and access to public services. In all these circumstances, it is extremely important that users actually end up on the website they intended to reach.
Domain names and top-level domains
All devices connected to the Internet have their own unique IP address, which consist of a long sequence of numbers. The Domain Name System links IP addresses to unique domain names.
Examples of domain names many use daily: dagbladet.no, vg.no, google.com and facebook.com.
The last part of the domain name – its “last name” – is the top-level domain the domain name is registered under. There are two different types of top-level domains: country code top-level domains (such as .no or .se) and generic top-level domains (such as .com, .org or .shop).
A website can be accessed in different ways: Clicking a link, via an app, via hits from a search engine, or entering the URL into a browser. All these methods of access entail looking up a domain name. The lookup initiates a search for an IP address used to contact the server operating the service you are requesting access to. Originally, the domain name system was not designed to ensure that the return for a lookup actually came from the right source. This means it is possible for attackers to falsify returns and direct a user to another IP address than the one associated with the domain name. For example, a user may be directed to a website that looks like the online retailer they intended to visit, but instead, the website is located on a server controlled by scammers.
What happens behind the scenes when you look up a domain name?
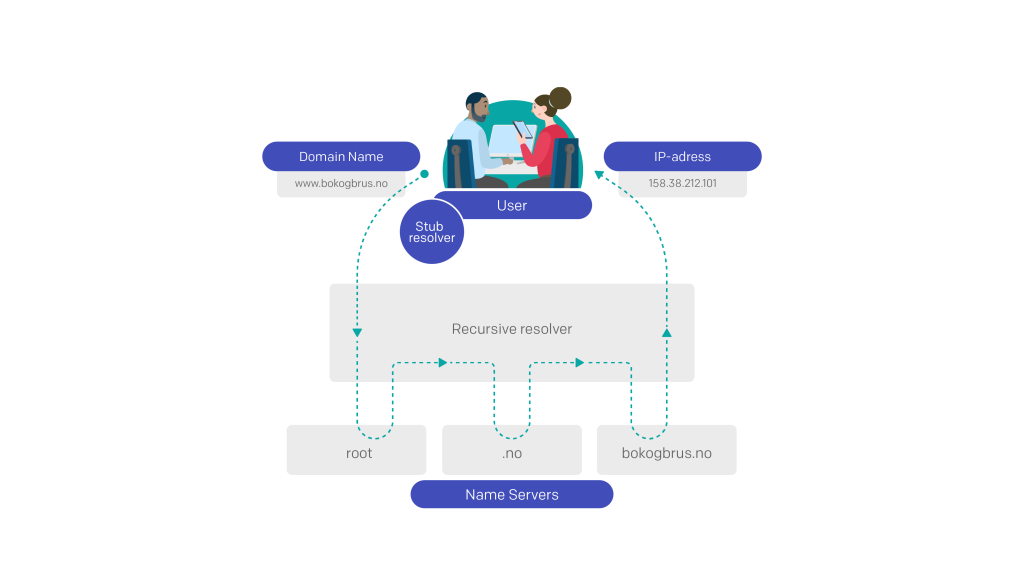
Each domain name has a set of servers handling queries about addresses under the domain name in question. These servers are called name servers.
- A small application in your device contacts a dedicated server set up to handle queries in the domain name system, a so-called recursive resolver (often operated by your Internet service provider).
- The recursive resolver is tasked with finding the IP address of www.bokogbrus.no. It forwards the query to one of the name servers for the top level of the domain name system (called the root). Root name servers only know the level below them in the hierarchy, and therefore returns a list of name servers for the top-level domain .no.
- The resolver then forwards the query to one of the name servers for .no. These servers also only know the level below them, and therefore return a list of name servers for bokogbrus.no.
- The resolver repeats the query to one of the name servers for bokogbrus.no, which returns the IP address for www.bokogbrus.no.
- The resolver then forwards the IP address to your device. Once your browser is provided with the IP address, it contacts the web server at this address, and downloads the website you requested.
The resolver normally accepts the first response to its query, and does not verify that it comes from the right source.
DNSSEC (DNS Security Extensions) is a security mechanism that offers a solution to this problem. When a domain name is secured by DNSSEC, all returns to domain queries will be signed cryptographically. This makes it possible to verify both that the response comes from the right source, and that it has not been changed along the way.
The signature is created by a private key accessible only to the operator of the domain name. The signature is validated by the device making the query in the domain name system retrieving a public key for the domain. It then pairs the key and signature to validate the answer. Given the hierarchy of the domain name system, a scammer cannot enter false keys in addition to false responses. The public key of a domain is part of an unbroken chain of keys validating each other, all the way to the top level. In order for DNSSEC to work, all levels have to be secured by DNSSEC. A chain is only as strong as its weakest link.
DNSSEC solves the problem of false responses to queries. It is important to be aware, however, that DNSSEC is only a small piece in a large puzzle of security measures needed to keep us safe online. DNSSEC ensures that we reach the address we wanted to reach, not that the contents of the site are safe.
Norway a world leader in securing the domain name system
Norid considers DNSSEC to be a key security component in the domain name system, and believes that the technology should be standard for Norwegian domain names. This approach to DNSSEC, however, requires sufficiently sophisticated technology so that there is extensive support for it. Norid has chosen to introduce DNSSEC as an infrastructure upgrade. A domain name subscriber is not supposed either to know about this technology or to order it for her or his domain name to benefit from this security upgrade.
Key DNSSEC milestones
2005: .se is the first top-level domain in the world to allow use of DNSSEC to secure its domain names. Because the top level of the domain name system had not yet been secured, .se had to create a temporary solution to compensate for this.
2010: The top level of the domain name system is secured by DNSSEC.
2014: Support for the technology is available in the most common software for domain name system queries. DNSSEC is implemented for Norwegian domain names.
Despite the need for sophisticated technology and limited room for errors, many registrars quickly came on board. In May 2015, six months after Norid introduced the technology, the Norwegian top-level domain was among the world’s leading top-level domains regarding percentage of secure domains, where it has remained since 1.
Share of domain names secured with DNSSEC
Key domain names still not signed
With more than half of all Norwegian domain names secured with DNSSEC, this technology has become a new standard here. Still, some of the most trafficked domain names are still not signed.
The ten most trafficked Norwegian domain names
| 1. | vg.no | not signed |
| 2. | finn.no | not signed |
| 3. | nrk.no | signed |
| 4. | dagbladet.no | not signed |
| 5. | google.no | not signed |
| 6. | tv2.no | not signed |
| 7. | yr.no | signed |
| 8. | nettavisen.no | not signed |
| 9. | difi.no | signed |
| 10. | e24.no | not signed |
Source: Similarweb
DNSSEC is a recommended standard for domain names registered by public administrative agencies in Norway 2. However, the public sector is lagging behind, with a somewhat lower degree of signing compared to the degree of signing for all Norwegian domain names. The gap has decreased in recent years, but public domain names are still not secured to the same extent as the rest of the domain names in society.
Development in the share of public domain names secured with DNSSEC
Large variance in the degree of signing among registrars
The share of registrars of Norwegian domain names that offers DNSSEC has increased over the last years.
Share of registrars offering security with DNSSEC
However, there are large differences in the degree of signing among the registrars. The majority of registrars have only signed a few percent of the domain names they manage, or do not offer such security of the customer's domain name. At the same time, there are some large registrars who offer the technology as part of their standard delivery, and who in sum ensure that more than half of all Norwegian domain names are signed.
Share of secured domain names among the ten largest registrars
| DOMENESHOP AS [NO] | 90.95% |
| GROUP.ONE NORWAY AS [NO] | 44.51% |
| One.com A/S [DK] | 91.67% |
| WEBHUSET AS [NO] | 0.00% |
| DOMENE AS [NO] | 1.04% |
| ASCIO TECHNOLOGIES, CORP. DANMARK - FILIAL AF ASCI | 0.94% |
| Name SRS AB [SE] | 2.63% |
| Telenor Norge AS [NO] | 85.63% |
| Abion AB [SE] | 1.67% |
| Corporation Service Company [US] | 3.07% |
At the forefront of validation as well
The large share of DNSSEC secured Norwegian domains means many domain lookups yield signed returns. In order for this to protect the individual user, however, the server retrieving the return for the domain query must check (validate) it, ensuring that returns containing false or inadequate signatures are rejected. This is handled by dedicated servers (recursive resolvers), which are often operated by Internet service providers, hosting providers and service supervisors of internal networks within an organization. In order to fully utilize the potential of DNSSEC, as many as possible of these providers must secure their users by enabling validation.
DNSSEC validation percentages by country
| Country | Percentage |
|---|---|
| AD | 25.55 |
| AE | 12.18 |
| AF | 59.61 |
| AG | 40.87 |
| AI | 74.33 |
| AL | 54.66 |
| AM | 75.49 |
| AO | 13.75 |
| AR | 27.37 |
| AS | 36.09 |
| AT | 14.12 |
| AU | 29.62 |
| AW | 85.83 |
| AX | 17.16 |
| AZ | 64.63 |
| BA | 22.58 |
| BB | 56.22 |
| BD | 71.03 |
| BE | 52.69 |
| BF | 75.51 |
| BG | 28.64 |
| BH | 22.82 |
| BI | 22.83 |
| BJ | 70.00 |
| BL | 0 |
| BM | 39.33 |
| BN | 21.87 |
| BO | 14.55 |
| BQ | 78.56 |
| BR | 52.38 |
| BS | 4.42 |
| BT | 95.15 |
| BW | 34.48 |
| BY | 27.55 |
| BZ | 49.18 |
| CA | 25.61 |
| CC | 0 |
| CD | 12.56 |
| CF | 95.66 |
| CG | 31.90 |
| CH | 66.04 |
| CI | 23.81 |
| CK | 9.04 |
| CL | 10.69 |
| CM | 33.10 |
| CN | 0.85 |
| CO | 19.80 |
| CR | 40.30 |
| CU | 3.92 |
| CV | 70.01 |
| CW | 12.11 |
| CY | 56.23 |
| CZ | 90.73 |
| DE | 65.34 |
| DJ | 96.55 |
| DK | 86.94 |
| DM | 21.48 |
| DO | 29.76 |
| DZ | 19.59 |
| EC | 36.96 |
| EE | 67.26 |
| EG | 13.66 |
| EH | 0 |
| ER | 22.03 |
| ES | 20.60 |
| ET | 9.98 |
| EU | 0 |
| FI | 95.46 |
| FJ | 96.21 |
| FK | 5.43 |
| FM | 90.29 |
| FO | 97.03 |
| FR | 53.95 |
| GA | 8.34 |
| GB | 17.76 |
| GD | 16.89 |
| GE | 19.73 |
| GF | 37.83 |
| GG | 81.42 |
| GH | 32.05 |
| GI | 83.28 |
| GL | 94.42 |
| GM | 39.93 |
| GN | 6.76 |
| GP | 16.17 |
| GQ | 40.51 |
| GR | 15.55 |
| GT | 21.69 |
| GU | 81.22 |
| GW | 2.15 |
| GY | 50.56 |
| HK | 56.12 |
| HN | 37.24 |
| HR | 10.56 |
| HT | 65.73 |
| HU | 7.13 |
| ID | 11.68 |
| IE | 34.36 |
| IL | 44.81 |
| IM | 26.12 |
| IN | 58.97 |
| IO | 92.09 |
| IQ | 67.96 |
| IR | 16.07 |
| IS | 91.89 |
| IT | 17.92 |
| JE | 46.87 |
| JM | 22.78 |
| JO | 3.42 |
| JP | 25.41 |
| KE | 26.59 |
| KG | 9.85 |
| KH | 52.25 |
| KI | 12.45 |
| KM | 79.98 |
| KN | 90.79 |
| KP | 0 |
| KR | 4.35 |
| KW | 31.80 |
| KY | 49.81 |
| KZ | 28.79 |
| LA | 26.46 |
| LB | 16.66 |
| LC | 40.01 |
| LI | 62.18 |
| LK | 5.76 |
| LR | 57.76 |
| LS | 44.71 |
| LT | 28.15 |
| LU | 79.92 |
| LV | 46.69 |
| LY | 49.61 |
| MA | 79.35 |
| MC | 7.71 |
| MD | 13.14 |
| ME | 11.33 |
| MF | 29.22 |
| MG | 25.84 |
| MH | 95.76 |
| MK | 15.97 |
| ML | 6.40 |
| MM | 40.37 |
| MN | 25.31 |
| MO | 5.36 |
| MP | 79.05 |
| MQ | 13.57 |
| MR | 23.01 |
| MS | 79.94 |
| MT | 22.85 |
| MU | 79.56 |
| MV | 47.33 |
| MW | 31.59 |
| MX | 9.92 |
| MY | 20.44 |
| MZ | 25.44 |
| NA | 47.77 |
| NC | 50.02 |
| NE | 49.23 |
| NF | 51.41 |
| NG | 9.07 |
| NI | 13.49 |
| NL | 62.09 |
| NO | 90.84 |
| NP | 29.02 |
| NR | 93.43 |
| NU | 0 |
| NZ | 90.11 |
| OM | 8.15 |
| PA | 8.82 |
| PE | 16.32 |
| PF | 84.50 |
| PG | 77.41 |
| PH | 24.01 |
| PK | 25.32 |
| PL | 49.62 |
| PM | 55.35 |
| PR | 15.61 |
| PS | 33.81 |
| PT | 32.27 |
| PW | 95.36 |
| PY | 43.38 |
| QA | 7.66 |
| RE | 16.65 |
| RO | 5.14 |
| RS | 40.51 |
| RU | 54.53 |
| RW | 25.11 |
| SA | 97.01 |
| SB | 16.82 |
| SC | 49.41 |
| SD | 5.20 |
| SE | 88.52 |
| SG | 76.39 |
| SH | 0 |
| SI | 44.27 |
| SJ | 0 |
| SK | 16.32 |
| SL | 97.13 |
| SM | 81.98 |
| SN | 6.78 |
| SO | 79.67 |
| SR | 24.18 |
| SS | 39.16 |
| ST | 29.82 |
| SV | 13.44 |
| SX | 63.79 |
| SY | 38.39 |
| SZ | 27.56 |
| TC | 19.36 |
| TD | 65.94 |
| TF | 0 |
| TG | 21.19 |
| TH | 7.33 |
| TJ | 45.52 |
| TL | 49.61 |
| TM | 38.96 |
| TN | 13.23 |
| TO | 51.89 |
| TR | 33.42 |
| TT | 13.49 |
| TV | 77.92 |
| TW | 7.06 |
| TZ | 37.21 |
| UA | 41.70 |
| UG | 16.97 |
| US | 36.63 |
| UY | 3.15 |
| UZ | 44.92 |
| VA | 0 |
| VC | 12.57 |
| VE | 42.71 |
| VG | 37.84 |
| VI | 25.85 |
| VN | 21.52 |
| VU | 38.77 |
| WF | 21.05 |
| WS | 97.72 |
| YE | 51.05 |
| YT | 36.63 |
| ZA | 40.19 |
| ZM | 14.40 |
| ZW | 45.39 |
The high degree of validation in Norway can be attributed to the fact that some major providers, such as Telenor Norge, Altibox and Get, whose total customer base is relatively large, have enabled validation. However, there are still some major providers, including GlobalConnect, that have not enabled validation 3.
DNSSEC and the future – what is possible with a secure infrastructure?
The immediate effect of DNSSEC is to safeguard users from false responses from the domain name system, but a secure domain name system also serves as a foundation on which we can build a whole new set of security features.
We are accustomed to being able to securely send email, even at airports, in Internet cafés and using guest networks, because our devices exchange data with the email server using a secure, encrypted connection that third parties cannot tap into or change. Similarly, we look for the green padlock symbol and HTTPS before transferring data such as credit card numbers, user names and passwords on websites we visit.
In order for these connections to be secure, our device must authenticate that it is communicating with the right service, and exchange the necessary cryptographic data. The authentication process largely relies on certificates issued by certificate authorities. The problem is that there are very many certificate authorities, and the level of security they offer varies considerably. Meanwhile, there has been a shortage of good mechanisms to inform users of which certificate authority is authorized to issue certificates for a given service, or which certificate or key the service in question uses. Google is among those who have experienced problems with this issue. In some cases, certificates have been issued for some of Google’s domain names that have not been authorized by Google 4. Such unauthorized certificates make it possible for someone to hijack or tap into traffic to the service.
The domain name system offers a possible solution to this problem. The system’s main purpose is to respond with the IP addresses of a service under a given domain, but the system can also provide certain types of additional information, such as which certificate authority is authorized to issue certificates for a given service 5. DNSSEC enables the user’s device to trust this information, instead of having to accept certificates from every certificate authority.
This application is particularly relevant in Norway, seeing as we have already implemented DNSSEC to a relatively large degree, and most social critical services are available online. Public authorities have a large number of online services for communication with the nation’s residents. The Norwegian National Security Authority recommends that all these should be secured with this technology, using certificates issued by certificate authorities subject to Norwegian law 6. The need for public websites to securely be able to communicate which certificate authorities they use is therefore quite pressing.
Email is another service that has started using information from the domain name system to increase security. Email servers that use certificates to prevent tapping need information about which certificates are in use for a domain name. In addition, the domain name system can be used to pass on which IP addresses are authorized to send email from a given domain name. And then how such email should be controlled, which makes it easier for a recipient to identify and reject email with forged sender address 7.
In the future, the distribution of secure information about services through the domain name system may extend the use of more security functionality for existing as well as for new services.
From theory to practice – some tools to check your DNSSEC status
Check to see if a Norwegian domain name is secured using DNSSEC.
Enter the domain name and see if it has been secured by DNSSEC, or enter an organization number to see the DNSSEC status of all the domain names of the organzation.
Find a registrar that can secure your domain names with DNSSEC.
Choose to show only providers that offer DNSSEC.
Sources
-
1.
CENTR. (Figures from July 2022)
Comparison between top-level domains with more than a thousand domain names - 2. Norwegian Digitalisation Agency (2015) «Referansekatalogen – grunnleggende datakommunikasjon»
- 3. Apnic labs. (Figures from 7 July 2022)
- 4. See examples of such cases here: arstechnica.com, arstechnica.com and security.googleblog.com
- 5. Internet Society (2012) «The DANE Protocol – DNS-Based Authentication of Named Entitiess»
- 6. Norwegian National Security Authority (2016) «Prosjektrapport – HTTPS for offentlige webtjenester»
- 7. Norwegian National Security Authority (2017) «Grunnleggende tiltak for sikring av e-post»
